Difference between revisions of "Adding local users"
m |
|||
| (16 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
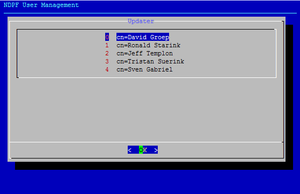
| − | + | [[Image:Ndpfuseradd-selectDN.png|thumb|Select your DN in the first screen, and give your LDAP management password]] | |
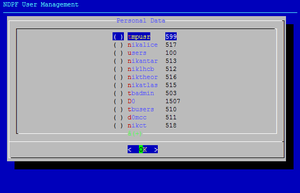
| + | [[Image:Ndpfuseradd-selectGid.png|thumb|Select the Unix group for the new user]] | ||
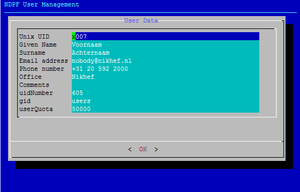
| + | [[Image:Ndpfuseradd-uinfo.png|thumb|Provide the new user's personal information, unix group (override) and initial quota]] | ||
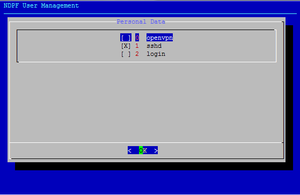
| + | [[Image:Ndpfuseradd-services.png|thumb|Select the services (pam) the user is allowed to use. If you select sshd, you can also provide one ssh public key for the user that will be added to LDAP and the authorized_keys file]] | ||
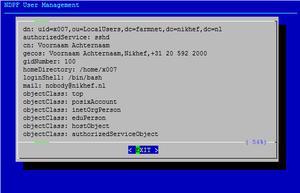
| + | [[Image:Ndpfuseradd-review.png|thumb|Final review screen. Press CTRL-C here if you see mistakes at this stage]] | ||
| − | + | An interactive 'ndpfuseradd' script is now available (from the ndpfsvn) and is installed (via RPMs) in /usr/local/sbin/ on relevant (trebbia, breg), but can be installed anywhere if you like. | |
| − | + | Prerequisites for using this tool: | |
| + | * you must have your ssh key in an agent (and you must be able to login as the provisioning user via ssh on the file server hosting the end-user home directories, if so configured for your account in <tt>~/.ndpfpooladdrc</tt>) | ||
| + | * you must be in the list of LDAP managers | ||
| + | * the tool (and the RPM dependencies) require perl-LDAP, perl-IO-Socket-SSL, perl-Net-SSLeay, and the 'dialog' command | ||
| − | |||
| − | + | Then start the tool - it's fully interactive. Login first, then select the (unix) group you want to add the new user to, and then complete the personal details. Have the new user's SSH key handy and it will be automatically inserted as well. It's simple now: | |
| − | + | /usr/local/sbin/ndpfuseradd | |
| − | /home | + | |
| − | and the | + | Just before committing the new entries to LDAP and the NFS server, you'll get to review the new entries. If you don't like them, press CTRL-C (pressing <tt>ESC</tt> twice to exit will exit at any dialog box, but is not enough here), and you're in the clear. |
| + | Also, some basic sanity checks are built in, but you can likely break the tool if you want to. | ||
| + | |||
| + | Usage: ndpfuseradd [-v[v..]] [-h] [-H ldapurl] [-b ldapbase] [-c config] [-u CN] | ||
| + | [--minuid n] [--maxuid n] [--maxgid n] [--days n] [--longuids] [--generic] | ||
| + | [-N|--nextfreeuid] | ||
| + | |||
| + | Interactive curses/tui utility to add users to the NikIdM directory and | ||
| + | trigger provisioning of core services (home, mail, printing, scanning) through | ||
| + | provisioning hooks. | ||
| + | |||
| + | Options: | ||
| + | -u CN common name of you as a Registrar (otherwise, a | ||
| + | dialog box will be shown with options) | ||
| + | -N just show the next free UID number and terminate | ||
| + | --longuids exceptionally allow usernames > 8 characters (for | ||
| + | generic "adm*" accounts only) | ||
| + | --generic create a generic account instead of a LocalUsers one | ||
| + | noting that you SHOULD MOVE the entry afterwards to | ||
| + | the proper subtree in the DIT | ||
| + | --days n New account will be valid to next <n> days | ||
| + | (default: 34128000). If user is also in P&O database, this | ||
| + | will be synched regardless of the number given here | ||
| + | --minuid n lowest uid number that will be considered/searched | ||
| + | (default: 10000) | ||
| + | --maxuid n highest uid number that will be considered/searched | ||
| + | (default: 20000) | ||
| + | |||
| + | == Sources == | ||
| + | |||
| + | In subversion: | ||
| + | https://ndpfsvn.nikhef.nl/repos/ndpf/nl.nikhef.ndpf.tools/ndpfuseradd/ | ||
| + | and the RPMs are at | ||
| + | http://www.nikhef.nl/grid/ndpf/files/local/packages/ | ||
| + | ''(and for the NDPF Quattor-managed systems on stal at http://stal.nikhef.nl/mirror/nikhef/ndpfuseradd-VER-REL.noarch.rpm)'' | ||
| + | |||
| + | |||
| + | <hr> | ||
| + | I tried extracting the list of managers automatically, but after having secured the LDAP server so that anonymous users can no longer glance such information with a single ldapsearch, I found myself in a catch22 situation (you need to bind to directory in order to see who you can bind as ...). Too bad, but I agree it still needs a configuration file instead of a hard coded list in the script. Will work on this. | ||
Latest revision as of 12:40, 19 March 2021
An interactive 'ndpfuseradd' script is now available (from the ndpfsvn) and is installed (via RPMs) in /usr/local/sbin/ on relevant (trebbia, breg), but can be installed anywhere if you like.
Prerequisites for using this tool:
- you must have your ssh key in an agent (and you must be able to login as the provisioning user via ssh on the file server hosting the end-user home directories, if so configured for your account in ~/.ndpfpooladdrc)
- you must be in the list of LDAP managers
- the tool (and the RPM dependencies) require perl-LDAP, perl-IO-Socket-SSL, perl-Net-SSLeay, and the 'dialog' command
Then start the tool - it's fully interactive. Login first, then select the (unix) group you want to add the new user to, and then complete the personal details. Have the new user's SSH key handy and it will be automatically inserted as well. It's simple now:
/usr/local/sbin/ndpfuseradd
Just before committing the new entries to LDAP and the NFS server, you'll get to review the new entries. If you don't like them, press CTRL-C (pressing ESC twice to exit will exit at any dialog box, but is not enough here), and you're in the clear. Also, some basic sanity checks are built in, but you can likely break the tool if you want to.
Usage: ndpfuseradd [-v[v..]] [-h] [-H ldapurl] [-b ldapbase] [-c config] [-u CN]
[--minuid n] [--maxuid n] [--maxgid n] [--days n] [--longuids] [--generic]
[-N|--nextfreeuid]
Interactive curses/tui utility to add users to the NikIdM directory and
trigger provisioning of core services (home, mail, printing, scanning) through
provisioning hooks.
Options:
-u CN common name of you as a Registrar (otherwise, a
dialog box will be shown with options)
-N just show the next free UID number and terminate
--longuids exceptionally allow usernames > 8 characters (for
generic "adm*" accounts only)
--generic create a generic account instead of a LocalUsers one
noting that you SHOULD MOVE the entry afterwards to
the proper subtree in the DIT
--days n New account will be valid to next <n> days
(default: 34128000). If user is also in P&O database, this
will be synched regardless of the number given here
--minuid n lowest uid number that will be considered/searched
(default: 10000)
--maxuid n highest uid number that will be considered/searched
(default: 20000)
Sources
In subversion:
https://ndpfsvn.nikhef.nl/repos/ndpf/nl.nikhef.ndpf.tools/ndpfuseradd/
and the RPMs are at
http://www.nikhef.nl/grid/ndpf/files/local/packages/ (and for the NDPF Quattor-managed systems on stal at http://stal.nikhef.nl/mirror/nikhef/ndpfuseradd-VER-REL.noarch.rpm)
I tried extracting the list of managers automatically, but after having secured the LDAP server so that anonymous users can no longer glance such information with a single ldapsearch, I found myself in a catch22 situation (you need to bind to directory in order to see who you can bind as ...). Too bad, but I agree it still needs a configuration file instead of a hard coded list in the script. Will work on this.