Difference between revisions of "CILogon Pre-Pilot Work"
(demo portal) |
(demo portal / architecture) |
||
| Line 11: | Line 11: | ||
== Demonstration Portal == | == Demonstration Portal == | ||
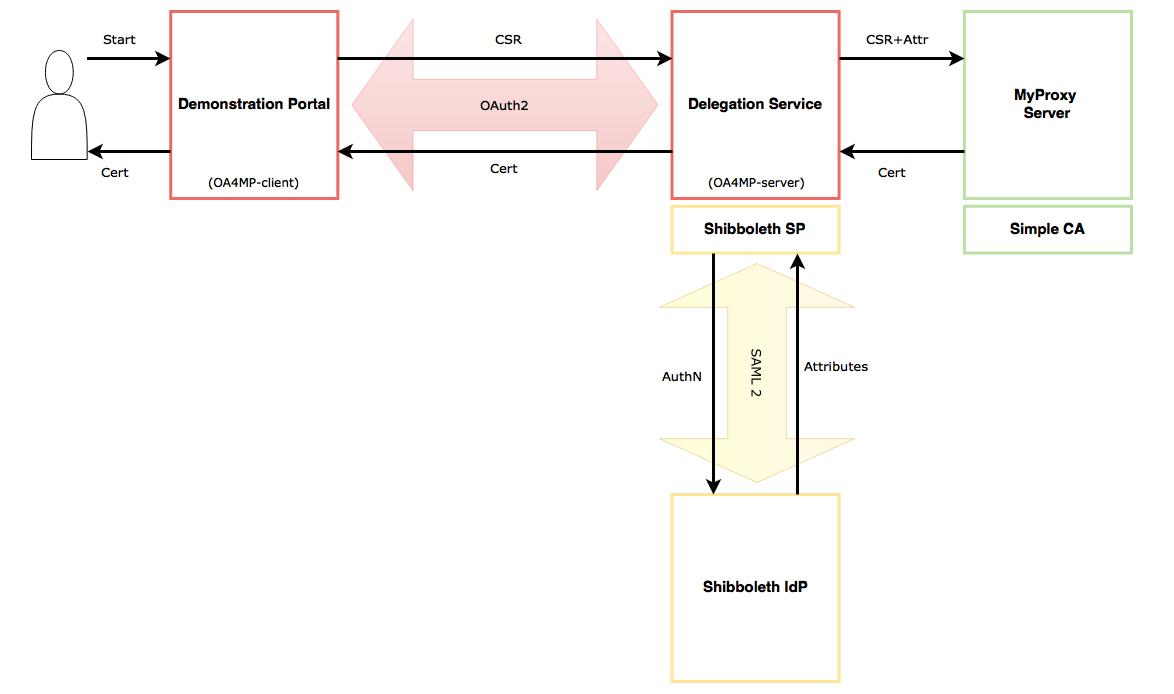
| − | We aimed our first use case at setting up a Demonstration Portal through which authenticated users can retrieve x509 certificates. This setup mimics the [https://demo.cilogon.org/ CILogon Portal Demonstration]. | + | We aimed our first use case at setting up a Demonstration Portal through which authenticated users can retrieve x509 certificates. This setup mimics the [https://demo.cilogon.org/ CILogon Portal Demonstration]. The user goes to the Demonstration Portal and starts the flow by asking for a certificate. The Demonstration Portal creates a new private key and a certificate signing request (CSR). The private key is sent back to the user, while the CSR is sent to the Delegation Service (acting as an online CA). At the Delegation Service the user gets redirected to his home IdP for authentication (for now there is only one single IdP in our setup). After authentication and consent the user attributes are sent to the Delegation Service. The Delegation Service uses MyProxy-Server (CA) to create a user certificate from the CSR and user attributes. This certificate is then sent back to the user. |
| + | === Components === | ||
| − | [[File:aarc-cilogon- | + | CILogon is based on [http://grid.ncsa.illinois.edu/myproxy/oauth/ OAuth for MyProxy] (OA4MP). For the purpose of this Demonstration Portal we used OA4MP because it's much better documented then setting up CILogon itself, and because it was the recommended way to go by Jim Basney (CILogon). |
| + | |||
| + | * [http://grid.ncsa.illinois.edu/myproxy/oauth/ OA4MP] : using both the client and the server components from the latest OAuth 2.0 implementation (3.1.1) | ||
| + | * [https://wiki.shibboleth.net/confluence/dashboard.action Shibboleth] : using the latest Identity Provider (3.0), and Service Provider (2.0) | ||
| + | * [http://grid.ncsa.illinois.edu/myproxy/ca/ MyProxy Server] : using official releases from epel (6.1.13) | ||
| + | * [http://toolkit.globus.org/toolkit/docs/latest-stable/simpleca/ SimpleCA] : using official release from epel (4.20) | ||
| + | |||
| + | === Architecture === | ||
| + | |||
| + | [[File:aarc-cilogon-demoportal.jpg]] | ||
Revision as of 14:24, 4 August 2015
Introduction
AARC is a European research and collaboration project which explores the possible future generation of authentication and authorization methods used in the grid world. CILogon is a candidate AAI component within this project. This document is the starting point of a piloting work on CILogon which will eventually evolve into a larger scale demonstration of the capabilities of this software product.
CILogon is an open source project used to provide x509 certificates based on the authenticated user's federated identity. These retrieved credentials are then meant to be used as authentication in further interactions with grid services.
We used Jenkins together with OpenStack to build an automatically deploying demo instance. Jenkins VM Image templates are used to boot VMs with relevant software installed on it, while separate Jenkins jobs are used to carry out different stages of the service deployment.
Use Cases
Demonstration Portal
We aimed our first use case at setting up a Demonstration Portal through which authenticated users can retrieve x509 certificates. This setup mimics the CILogon Portal Demonstration. The user goes to the Demonstration Portal and starts the flow by asking for a certificate. The Demonstration Portal creates a new private key and a certificate signing request (CSR). The private key is sent back to the user, while the CSR is sent to the Delegation Service (acting as an online CA). At the Delegation Service the user gets redirected to his home IdP for authentication (for now there is only one single IdP in our setup). After authentication and consent the user attributes are sent to the Delegation Service. The Delegation Service uses MyProxy-Server (CA) to create a user certificate from the CSR and user attributes. This certificate is then sent back to the user.
Components
CILogon is based on OAuth for MyProxy (OA4MP). For the purpose of this Demonstration Portal we used OA4MP because it's much better documented then setting up CILogon itself, and because it was the recommended way to go by Jim Basney (CILogon).
- OA4MP : using both the client and the server components from the latest OAuth 2.0 implementation (3.1.1)
- Shibboleth : using the latest Identity Provider (3.0), and Service Provider (2.0)
- MyProxy Server : using official releases from epel (6.1.13)
- SimpleCA : using official release from epel (4.20)