Difference between revisions of "GLExec"
From PDP/Grid Wiki
Jump to navigationJump to search| (179 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
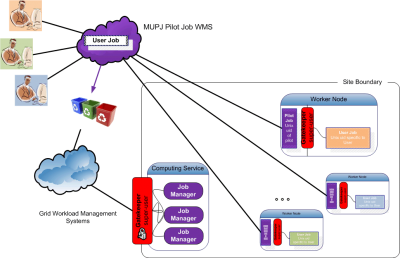
| − | gLExec is a program to | + | [[Image:MUPJ-CE-WN-gLExec.png|thumb|upright|400px|Multi User Pilot Job with CE & WN]] gLExec is a program that acts as a light-weight 'gatekeeper'. gLExec takes Grid credentials as input. gLExec takes the local site policy into account to '''authenticate''' and '''authorize''' the credentials. gLExec will switch to a new execution '''sandbox''' and execute the given command as the switched identity. gLExec is also capable of functioning as a light-weight control point which offers a binary ''yes''/''no'' result called the logging-only mode. |
| − | gLExec | + | == Current gLExec version == |
| − | The | + | The latest stable versions released are: |
| + | * gLite-3.2: 0.8.1 | ||
| + | * EMI-1: 0.8.10 | ||
| + | * EMI-2: 0.9.6 | ||
| + | * EMI-3: 0.9.11 | ||
| − | + | Latest version available: 0.9.11, released in EMI-3 and UMD-3. Latest OSG release [https://www.opensciencegrid.org/bin/view/Documentation/Release3/WebHome OSG-3] is 0.9.9. | |
| − | = | + | == User information == |
| − | + | * [[Proxy file handling in gLExec]] What do all the '''environment variables''' do with '''proxy''' files | |
| + | * [[GLExec TransientPilotJobs]] describes how you may go about managing a '''target''' workload's '''directory''' in '''Pilot Job Frameworks'''. | ||
| + | * [[GLExec Environment Wrap and Unwrap scripts]] describes how you can '''preserve''' the '''environment''' variables between the calling process of gLExec and the user switched side of gLExec. For example: to preserve the environment variables from a Pilot Job Framework, through gLExec and into Pilot Job Payload. | ||
| − | + | === Documentation === | |
| − | * | + | * [[Exit codes of gLExec]] |
| + | * [[Man pages of gLExec]] | ||
| − | * | + | * EMI-2 and EMI-3 information: |
| + | ** [http://www.nikhef.nl/grid/lcaslcmaps/EMI2_docs/glexec_userguide.pdf EMI-2 User Guide PDF] | ||
| − | + | == Sysadmin information == | |
| − | + | === Deployment: Installation and setups === | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | * gLExec on the Worker Nodes or Computing Element | |
| + | ** [[Using generic per-node pool accounts or a shared map database]] | ||
| + | ** [[GLExec Argus Quick Installation Guide]] | ||
| + | ** [[Using the SCAS]] | ||
| + | ** [[Batch System Interoperability]] | ||
| + | ** [[LCMAPS Tracking GroupID plugin]] | ||
| + | * [[Deployment Scenarios in EGEE and OSG]] | ||
| + | * [[Secure installation considerations]] | ||
| + | * [[Debugging hints]] | ||
| + | * [[GLExec Epilogue Functionality]] (version 0.9 and up) | ||
| − | + | * To help you master gLExec's security: | |
| + | ** [[Need to Know's]]: Explains about the '''LD_LIBRARY_PATH''' in combo with '''setuid''' programs. | ||
| + | ** [https://www.nikhef.nl/pub/projects/grid/gridwiki/images/a/ab/Argus-SCAS-note-20100602.pdf Argus and SCAS node dd. June 2nd, 2010]: quick guide on how to decide for either SCAS or Argus as the central service with gLExec. | ||
| − | + | * [[FAQs and misconceptions about gLExec]] | |
| − | + | See also the [[#Background information|Background information]] | |
| − | + | === To help you adapt or rebuild gLExec === | |
| − | * | + | * [[Building gLExec and its gLite dependencies from SVN source]] How to build gLExec and all its gLite dependencies directly from source. |
| − | + | * [[Building gLExec from src rpm]] How to build gLExec from a source RPM. | |
| − | * | ||
| − | + | === Documentation === | |
| − | + | * [[Man pages of gLExec]] | |
| + | * [[Service Reference Card for gLExec]] | ||
| + | * [[Papers about gLExec]] | ||
| − | + | See also the [[#Background information|Background information]] | |
| − | + | * EMI-2 and EMI-3 information: | |
| + | ** [http://www.nikhef.nl/grid/lcaslcmaps/EMI2_docs/glexec_funcdesc.pdf EMI-2 Functional Description PDF] | ||
| + | ** [http://www.nikhef.nl/grid/lcaslcmaps/EMI2_docs/glexec_servrefcard.pdf EMI-2 Service Reference Card PDF] | ||
| + | ** [http://www.nikhef.nl/grid/lcaslcmaps/EMI2_docs/glexec_sysadminguide.pdf EMI-2 System Administrator's Guide PDF] | ||
| − | + | == Test plans/reports == | |
| − | + | * [[EMI-1 gLExec release test report]]: This is the report describing the test performed for the software certification of the released components with gLExec. | |
| − | + | * [[EMI-2 gLExec release test report]]: This is the report describing the test performed for the software certification of the released components with gLExec. | |
| − | |||
| − | |||
| − | |||
| − | + | == Background information == | |
| − | + | * [https://twiki.cern.ch/twiki/bin/view/LCG/GlexecDeployment LCG Deployment of gLExec on the Worker Node] | |
| − | + | * [https://wlcg-tf.hep.ac.uk/wiki/Multi_User_Pilot_Jobs Multi User Pilot Jobs] | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | * | ||
| − | |||
| − | * | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
Latest revision as of 10:19, 4 March 2015
gLExec is a program that acts as a light-weight 'gatekeeper'. gLExec takes Grid credentials as input. gLExec takes the local site policy into account to authenticate and authorize the credentials. gLExec will switch to a new execution sandbox and execute the given command as the switched identity. gLExec is also capable of functioning as a light-weight control point which offers a binary yes/no result called the logging-only mode.
Current gLExec version
The latest stable versions released are:
- gLite-3.2: 0.8.1
- EMI-1: 0.8.10
- EMI-2: 0.9.6
- EMI-3: 0.9.11
Latest version available: 0.9.11, released in EMI-3 and UMD-3. Latest OSG release OSG-3 is 0.9.9.
User information
- Proxy file handling in gLExec What do all the environment variables do with proxy files
- GLExec TransientPilotJobs describes how you may go about managing a target workload's directory in Pilot Job Frameworks.
- GLExec Environment Wrap and Unwrap scripts describes how you can preserve the environment variables between the calling process of gLExec and the user switched side of gLExec. For example: to preserve the environment variables from a Pilot Job Framework, through gLExec and into Pilot Job Payload.
Documentation
- EMI-2 and EMI-3 information:
Sysadmin information
Deployment: Installation and setups
- gLExec on the Worker Nodes or Computing Element
- Deployment Scenarios in EGEE and OSG
- Secure installation considerations
- Debugging hints
- GLExec Epilogue Functionality (version 0.9 and up)
- To help you master gLExec's security:
- Need to Know's: Explains about the LD_LIBRARY_PATH in combo with setuid programs.
- Argus and SCAS node dd. June 2nd, 2010: quick guide on how to decide for either SCAS or Argus as the central service with gLExec.
See also the Background information
To help you adapt or rebuild gLExec
- Building gLExec and its gLite dependencies from SVN source How to build gLExec and all its gLite dependencies directly from source.
- Building gLExec from src rpm How to build gLExec from a source RPM.
Documentation
See also the Background information
- EMI-2 and EMI-3 information:
Test plans/reports
- EMI-1 gLExec release test report: This is the report describing the test performed for the software certification of the released components with gLExec.
- EMI-2 gLExec release test report: This is the report describing the test performed for the software certification of the released components with gLExec.