Difference between revisions of "Agile testbed"
(Agile testbed moved to Agile testbed old) |
|||
| Line 1: | Line 1: | ||
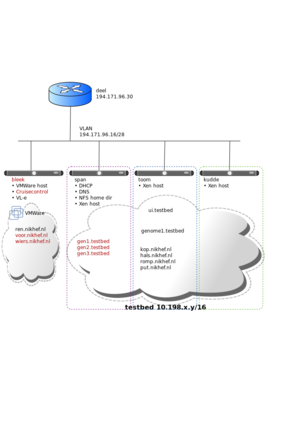
| − | + | [[Image:P4ctb.svg|thumb|Diagram of the agile test bed]] | |
| + | == Hardware == | ||
| + | |||
| + | |||
| + | [[NDPF_Node_Functions#P4CTB|The testbed]] currently consists of four physical machines: | ||
| + | bleek, toom, kudde and span. | ||
| + | |||
| + | {| class="wikitable" border="0" cellpadding="8" | ||
| + | |-style="background-color: #ccc;" | ||
| + | ! name | ||
| + | ! type | ||
| + | ! #cores | ||
| + | ! mem | ||
| + | ! OS | ||
| + | ! disk | ||
| + | ! remarks | ||
| + | |- | ||
| + | | bleek | ||
| + | | Intel 5150 @ 2.66GHz | ||
| + | | 4 | ||
| + | | 8GB | ||
| + | | CentOS4-64 | ||
| + | | software raid1 2×500GB disks | ||
| + | | High Availability, dual power supply | ||
| + | |- | ||
| + | | toom | ||
| + | | Intel E5440 @ 2.83GHz | ||
| + | | 8 | ||
| + | | 16GB | ||
| + | | CentOS5-64 | ||
| + | | Hardware raid1 2×715GB disks | ||
| + | |- | ||
| + | | kudde | ||
| + | | Intel E5440 @ 2.83GHz | ||
| + | | 8 | ||
| + | | 16GB | ||
| + | | CentOS5-64 | ||
| + | | Hardware raid1 2×715GB disks | ||
| + | |- | ||
| + | | span | ||
| + | | Intel E5440 @ 2.83GHz | ||
| + | | 8 | ||
| + | | 24GB | ||
| + | | CentOS5-64 | ||
| + | | Hardware raid10 on 4×470GB disks (950GB net) | ||
| + | | DHCP,DNS,NFS,LDAP | ||
| + | |} | ||
| + | |||
| + | |||
| + | == Network == | ||
| + | |||
| + | The network between these machines is a bit particular: They all live in the same VLAN (194.171.96.16/28) but they all have an extra alias interface in the 10.198.0.0/16 range. The Xen DomUs on each of the Xen machines that live in that address range are given connectivity to the other DomUs in the same VLAN without using NAT, and connectivity to the outside with SNAT. Here's an example of the iptables on span: | ||
| + | Chain POSTROUTING (policy ACCEPT 58M packets, 3693M bytes) | ||
| + | pkts bytes target prot opt in out source destination | ||
| + | 0 0 ACCEPT all -- any any 10.198.0.0/16 194.171.96.16/28 | ||
| + | 436 63986 ACCEPT all -- any any 10.198.0.0/16 10.198.0.0/16 | ||
| + | 1 190 SNAT all -- any any 10.198.0.0/16 anywhere to:194.171.96.28 | ||
| + | |||
| + | So all traffic from a DomU on span will appear to have come from span to the outside. | ||
| + | |||
| + | Note that DomUs that have interfaces in the public address range do not need SNAT at all, they simply connect to the hosts xen bridge. | ||
| + | |||
| + | There is a separate network attached to each machine to allow IPMI management and Serial-Over-Lan. | ||
| + | |||
| + | == Software Installation == | ||
| + | |||
| + | The central machine in the network is span, it runs | ||
| + | * dnsmasq for DNS and DHCP based on /etc/hosts and /etc/ethers | ||
| + | * NFS server for the home directories and ssh and pem host keys | ||
| + | |||
| + | The other Xen machines, toom and kudde, run Xen 3.1. On these machines the creation and destruction of virtual machines is best left to the generate-machine and destroy-machine scripts, part of the [https://gforge.vl-e.nl/plugins/scmcvs/cvsweb.php/nl.vl-e.poc.ctb.mktestbed/?cvsroot=build nl.vl-e.poc.ctb.mktestbed] software package. | ||
Revision as of 09:38, 28 August 2009
Hardware
The testbed currently consists of four physical machines: bleek, toom, kudde and span.
| name | type | #cores | mem | OS | disk | remarks |
|---|---|---|---|---|---|---|
| bleek | Intel 5150 @ 2.66GHz | 4 | 8GB | CentOS4-64 | software raid1 2×500GB disks | High Availability, dual power supply |
| toom | Intel E5440 @ 2.83GHz | 8 | 16GB | CentOS5-64 | Hardware raid1 2×715GB disks | |
| kudde | Intel E5440 @ 2.83GHz | 8 | 16GB | CentOS5-64 | Hardware raid1 2×715GB disks | |
| span | Intel E5440 @ 2.83GHz | 8 | 24GB | CentOS5-64 | Hardware raid10 on 4×470GB disks (950GB net) | DHCP,DNS,NFS,LDAP |
Network
The network between these machines is a bit particular: They all live in the same VLAN (194.171.96.16/28) but they all have an extra alias interface in the 10.198.0.0/16 range. The Xen DomUs on each of the Xen machines that live in that address range are given connectivity to the other DomUs in the same VLAN without using NAT, and connectivity to the outside with SNAT. Here's an example of the iptables on span:
Chain POSTROUTING (policy ACCEPT 58M packets, 3693M bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- any any 10.198.0.0/16 194.171.96.16/28
436 63986 ACCEPT all -- any any 10.198.0.0/16 10.198.0.0/16
1 190 SNAT all -- any any 10.198.0.0/16 anywhere to:194.171.96.28
So all traffic from a DomU on span will appear to have come from span to the outside.
Note that DomUs that have interfaces in the public address range do not need SNAT at all, they simply connect to the hosts xen bridge.
There is a separate network attached to each machine to allow IPMI management and Serial-Over-Lan.
Software Installation
The central machine in the network is span, it runs
- dnsmasq for DNS and DHCP based on /etc/hosts and /etc/ethers
- NFS server for the home directories and ssh and pem host keys
The other Xen machines, toom and kudde, run Xen 3.1. On these machines the creation and destruction of virtual machines is best left to the generate-machine and destroy-machine scripts, part of the nl.vl-e.poc.ctb.mktestbed software package.